Designed for use with BackTrack 5 R3, 32-bit gnome.
Updates
- Aug 20 - Added jigsaw to setup.sh.
- Aug 19 - Added goofile to the passive option for scrape.
- July 29 - Added crack-wifi.sh to framework.
- July 27 - Niko now takes a list of nmap greppable output.
- July 25 - Added color to update alias and framework.
- July 5 - Updated alias and setup.sh to reflect the new hosted location of sqlmap.
- June 28 - Fixed passive recon problems with Whois-IP and LinkedIn returning job titles.
- June 20 - After testing Metasploitable 2 by doing a full port scan, I noticed there were some ports missing from my default scan. The following TCP ports have been added: 1524, 6697, 8787, 41364, 48992, 49663, 59034.
- June 11 - Scrape now contains passive and active options.
- June 5 - Check 'notes' for a To-Do list
- June 4 - Added new option - niktos
Also included is a collection of python scripts by Saviour Emmanuel.
- Domain Parser
- Ghost DHCPD
- ghost-phisher
- mssql-lhf.py
How to use Script -
1. Download scripts to the proper location.
svn co https://backtrack-scripts.googlecode.com/svn/ /opt/scripts
2. Set permissions.
chmod +x /opt/scripts/ -R
3. Run the setup script.
cd /opt/scripts/./setup.sh
4. Exit Terminal and open a new one. Run the new alias to update the distro and commonly used applications. This should be ran daily.
update
5. Run the main application.
./discover.sh
______ ___ ______ ______ _____ _ _ ______ _____| \ | |____ | | | \ / |_____ |____/
|_____/ _|_ _____| |_____ |_____| \/ |_____ | \_
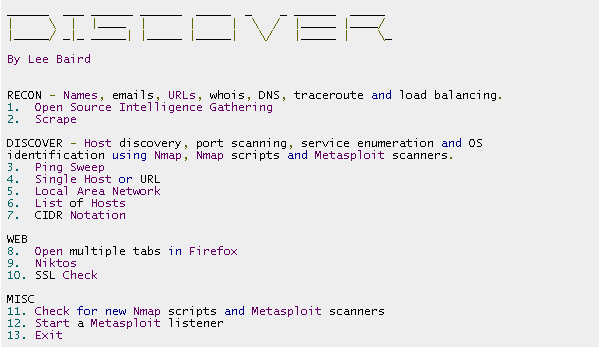
By Lee Baird
RECON - Names, emails, URLs, whois, DNS, traceroute and load balancing.
1. Open Source Intelligence Gathering
2. Scrape
DISCOVER - Host discovery, port scanning, service enumeration and OS
identification using Nmap, Nmap scripts and Metasploit scanners.
3. Ping Sweep
4. Single IP, URL or Range
5. Local Area Network
6. List
7. CIDR Notation
WEB8. Open multiple tabs in Firefox
9. Nikto
10. SSL Check
MISC11. Crack WiFi
12. Start a Metasploit listener13. Exit
Open Source Intelligence Gathering.
1. Company
2. Person
3. Previous menu
Scrape
1. Passive
2. Active
3. Previous menu
Open multiple tabs in Firefox with:
1. List containing IPs and/or URLs.
2. Directories from a domain's robot.txt.
3. Previous menu
Visit Website -
http://code.google.com/p/backtrack-scripts/
for more information -
http://code.google.com/p/backtrack-scripts/w/list
0 comments:
Post a Comment